HMAC
The key used to create the HMAC is your Webhook Secret, and you verify it by running the algorithm yourself with the payload and the key to re-create the HMAC.
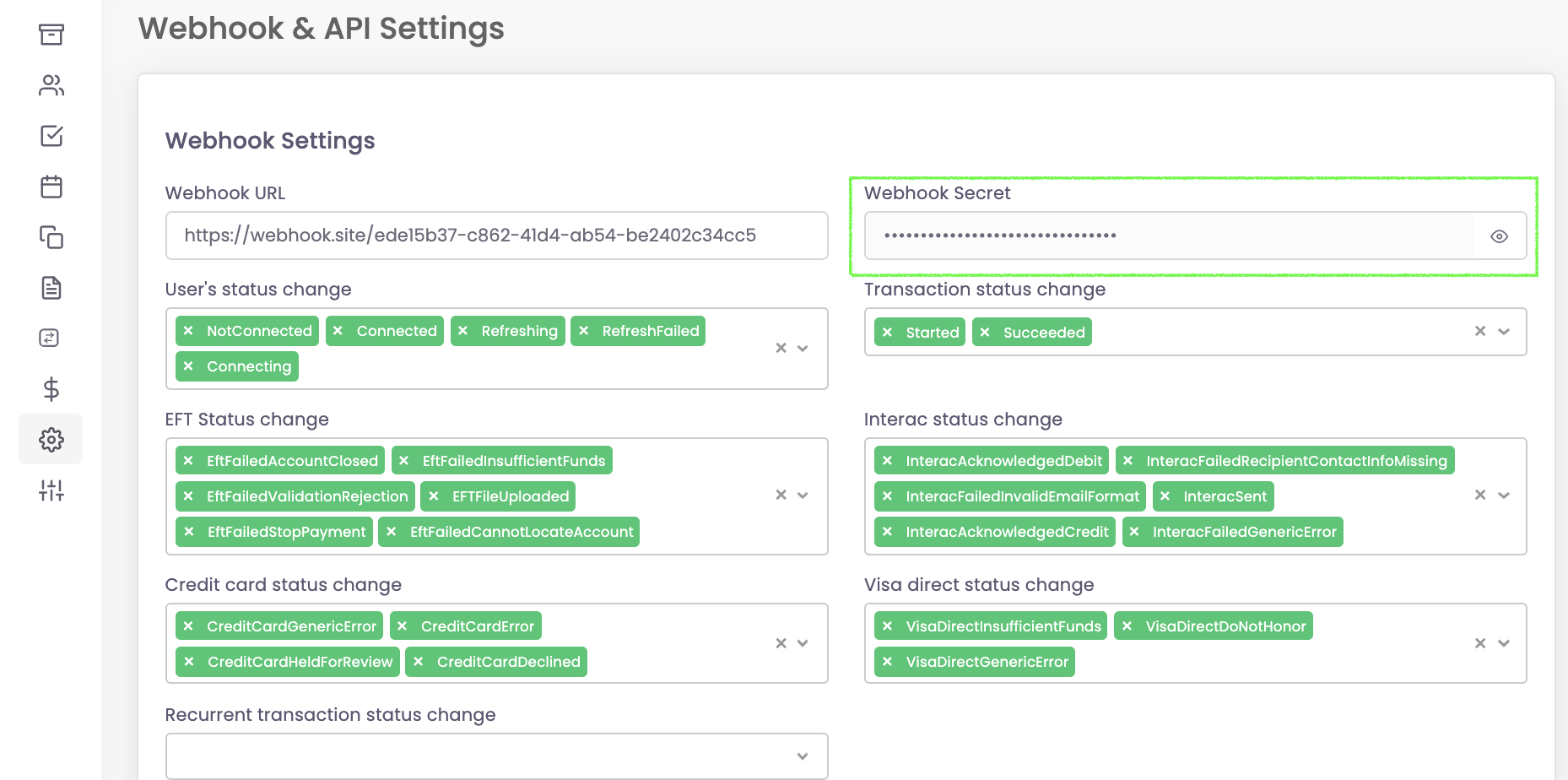
Your Webhook Secret can be found in the portal under your settings.
The signature is always sent with the webhook in a header named zumrails-signature
You can verify the authenticity of the webhook response by using HMAC.
The HMAC verification process is as follows:
- You receive a POST request via the webhook
- Your app computes a signature based on the payload received, using your Webhook Secret
- You verify that your signature matches the zumrails-signature in the request
Here are the steps to validate a request coming from Zum Rails
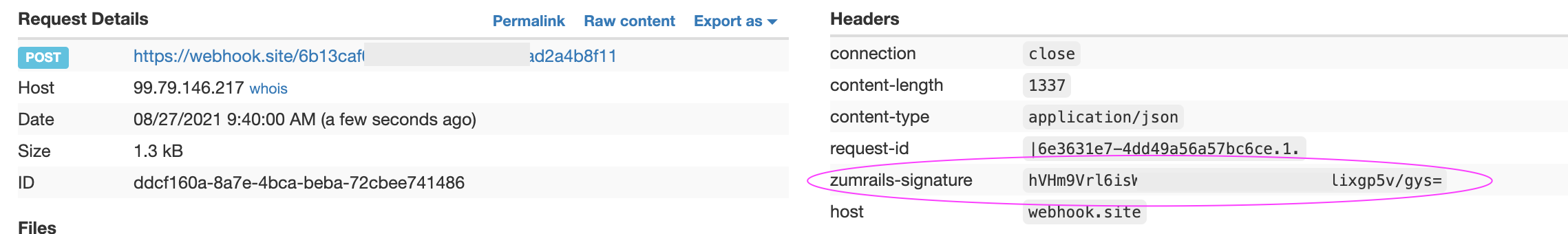
1) Retrieve the zumrails-signature header from the webhook:
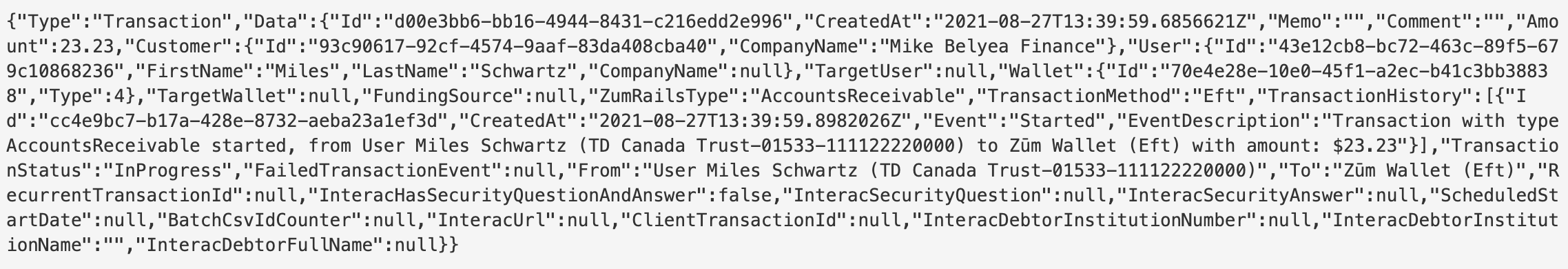
2) Retrieve the json body of the request. Make sure you are not adding any new spaces or formats. E.g:
3) Using HMAC SHA256 implemented in your programming language, calculate the signature on your side. The body is the payload and the secret is your Webhook Secret.
The output should be in Base64 format.
For your tests, you can use an online HMAC generator. https://www.liavaag.org/English/SHA-Generator/HMAC/ is one example.
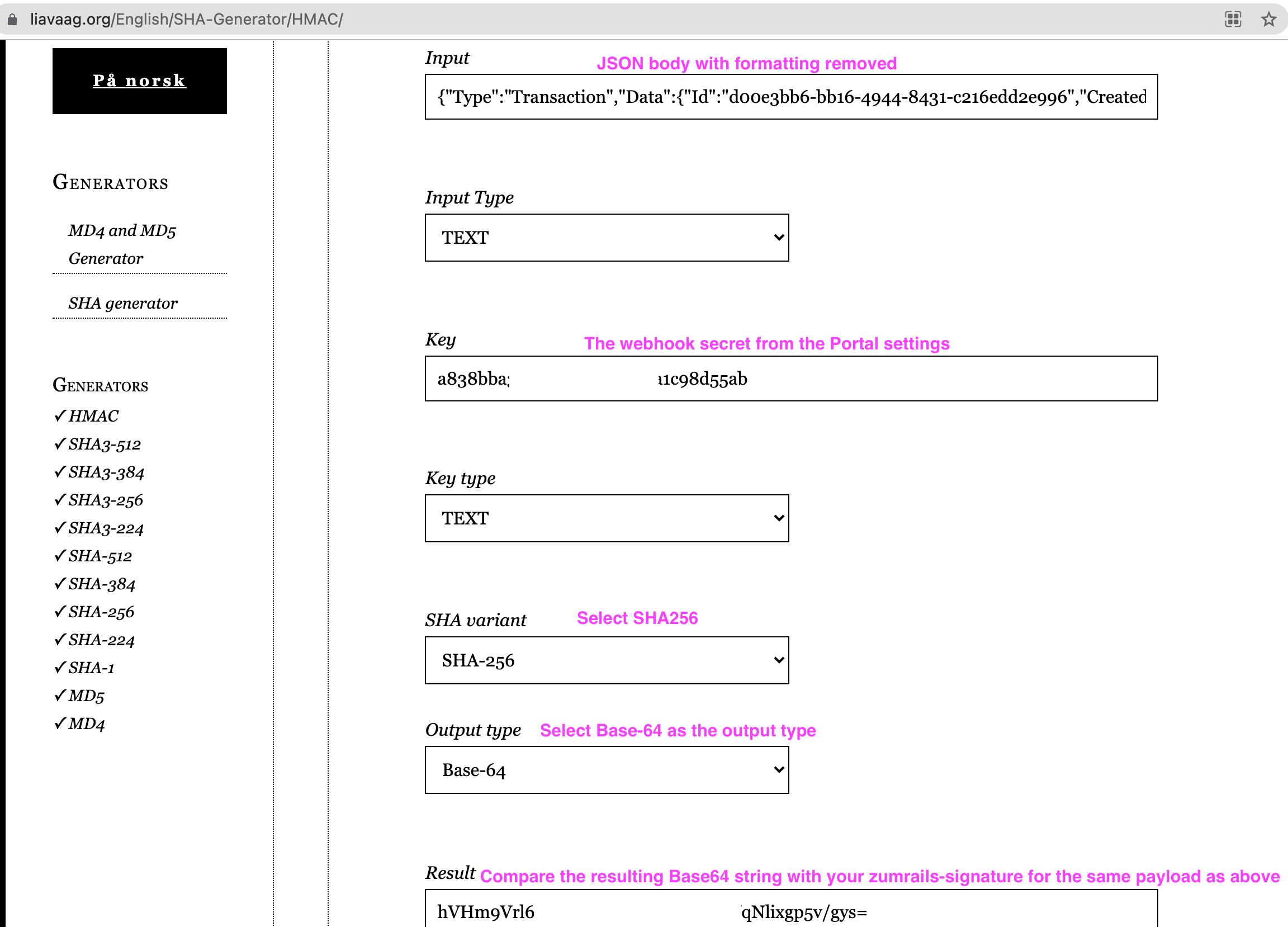
4) Compare your hash with the value provided under the zumrails-signature in the request, they should match. As you can see, the Result here (hV...gys=) matches the zumrails-signature in the screenshot from step (1) above.
A few examples of how to calculate HMAC in different languages: https://github.com/danharper/hmac-examples